Protecting a Device's Root Secrets with SRAM PUF
Geert-Jan Schrijen, CTO of Intrinsic ID, takes us back to basics and looks at how to protect a device’s most important secret, its cryptographic root key, with SRAM PUF technology.
This article was first published on
www.intrinsic-id.comVideo Transcription
Hello. My name is Geert-Jan Schrijen, CTO of Intrinsic ID. In this whiteboard video, we will go back to basics and look at how we can protect a device’s most important secret, its cryptographic root key, with SRAM PUF technology.
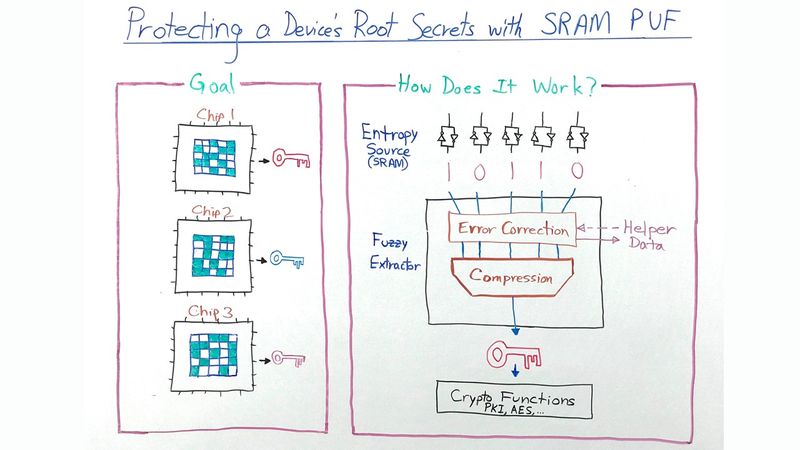
First of all, what is a PUF? In semiconductor chips, a physical unclonable function, or PUF, is an electronic design component that extracts unique silicon fingerprints from inherent process variations. These variations are hard to reproduce physically or clone. No one, not even the manufacturer, can reproduce them. So even though semiconductor chips are designed to be functionally equivalent across a production run, at the physics level they exhibit very unique behavior. This unique silicon fingerprint is used as the entropy source for generation of the chip’s cryptographic root key.
The most widely deployed PUF today is the SRAM PUF for three important reasons:
- It works with a standard circuit element, static random-access memory, or SRAM
- It is available in any digital chip
- And it’s not just a source of uniqueness but also provides randomness for cryptographic protocols.
So how does it work? A dedicated part of an SRAM memory is used as entropy source by reading out its uninitialized cell use after power-up. Every SRAM memory cell consists of two cross-coupled inverters, whose strengths vary due to process variations. When power is ramping up, these invisible variations cause every cell to express their preferred power-up states, either a zero or one. The power-up pattern is unique for every memory but also highly repeatable for the same memory, except for some noise.
To generate a reliable root key from the SRAM PUF entropy source, an algorithm known as a fuzzy extractor is used. It has two main functions: power correction, to eliminate the noise, and compression, to make sure that the full entropy key is obtained.
A fuzzy extractor supports two main operations: enrollment and reconstruction. At enrollment, the PUF response is read out for the first time, and device-unique helper data and root key are generated. This helper data contains no secrets and can be stored anywhere in the clear, even in the cloud. At reconstruction, a new noisy PUF measurement is done and combined with the helper data to reconstruct the same root key on the fly.
The fuzzy extractor is the main component in Intrinsic ID’s QuiddiKey and BK Software IP products. An important security advantage is the fact that no sensitive data is kept inside the chip when the power is switched off. Note that this is not the case for keys stored in nonvolatile memory such as fuses or antifuses. Those keys can be retrieved by a physical attacker, destructively reverse engineering the chip.
Unlike most other PUFs, a correctly designed SRAM PUF with its fuzzy extractor is agnostic to fab, nodes, and speed of the chip. This ease of use yields great benefits for ROI and time to market.
Thank you for your attention and look for more whiteboard videos from Intrinsic ID.