Understanding Low-Cost IoT Attacks
The risk of low-cost IoT attacks demands vigilance and innovation.

This is the first article in a 4-part series based on a whitepaper published by Intrinsic ID that dives deep into such low-cost IoT attacks. The series will cover the origin of the low-cost attacks, their types, preventions, security assurance, how to ensure IoT platform security, IC lifecycle, and how it impacts IC's safety. The first article will examine low-cost IoT attacks from their conceptual foundation.
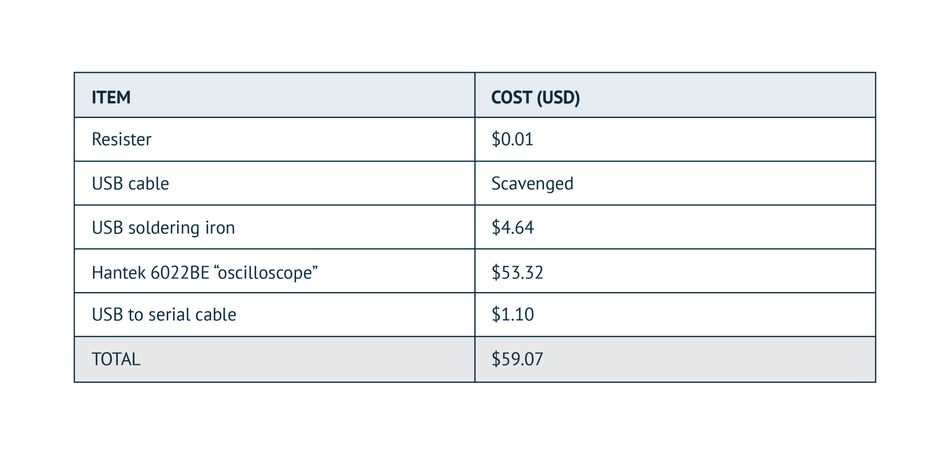
In 2018, Rafael Boix Carpi attacked a general-purpose microcontroller device, broke the AES encryption, and unveiled the messages being sent. He wasn’t the first successful attacker to do so, but he’d made a stunning discovery - he could hijack an IoT device with almost zero resources. The attack had cost less than $60. The table below shows the cost breakdown of Rafael's attack.
Vulnerable IoT and Low-Cost IoT Attacks
By 2025, there will likely be more than 27 billion IoT connections across industries as broad as agriculture, manufacturing, transportation and logistics, healthcare, energy, smart homes, and smart cities. The global IoT market is expected to reach USD 1.39 Trillion by 2026.(1)
These devices enable an unprecedented era of rapid automation and data-driven insight and decision making. Simultaneously the advent of IoT presents new aspects of vulnerability to businesses and organizations. According to a cyber solutions company Kaspersky, an analysis of its telemetry from honeypots revealed that more than 1.5 billion IoT attacks were detected in 2021– up from 639 million during the first half of 2020.(2)
Types of IoT Attackers
The people performing attacks on IoT devices can be broadly organized into four main categories.
Governmental Attackers. Sophisticated IoT attacks against governments or large industries are very hard to defend against.
Security Researchers. Security researchers such as Carpi dedicate time to search for hidden, easy-to-exploit vulnerabilities to raise awareness for the industry and expand IoT security knowledge.
Script Gurus. Usually, these are groups of technically curious people who often have no malicious agenda. Companies may reward these types of investigations with bug bounties.
Criminal attackers. Attacks are motivated by commercial gain, either through theft of information or holding an institution to ransom. In the case of the former, the attack can go unnoticed for years.
In all these cases, the damage caused by the attacks can be extensive, expensive and create public distrust that can last for years. But the most troubling part is that many attacks can be performed at very low cost. While Governmental Attackers have virtually unlimited resources and Security Researchers might have expensive lab equipment, most attacks on IoT devices (like the one by Carpi) show that there often is no need for deep pockets when it comes to compromising IoT devices. The fact that many IoT attacks only require limited investment is the biggest threat to our connected world, because it allows anyone to be a potential attacker. That is why this series will be focusing on low-cost attacks and how they can be prevented. This first article describes the types of low-cost attacks known to be used on IoT devices.
Types of Low-Cost Attacks
Low-cost physical attacks are inexpensive gateways to launch large-scale attacks, especially if all IoT devices have the same root/master key. One is attacked, all are brought down, bringing tremendous financial benefits for the attackers.
Low-cost IoT attacks belong to four main categories, indicated in the grid below:
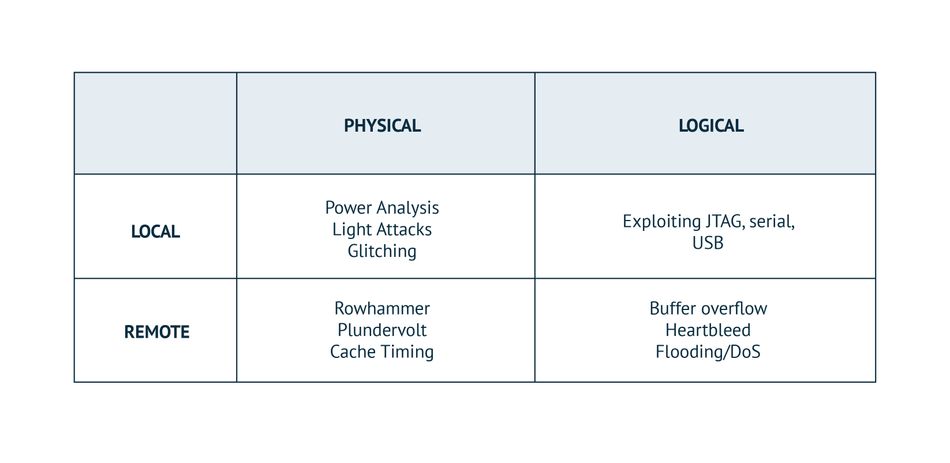
The following paragraphs discuss these low-cost attacks in detail.
Local Physical Attacks
In physical attacks, the attacker accesses operating embedded devices to gain insights into their specifications. These insights might include the device's firmware, power consumption, etc. These specs are then exploited to launch attacks.
Three types of local physical attacks gained popularity in recent years:
Side Channel Attack (SCA)
Fault Injection Attack (FIA)
Invasive Attacks
Side-Channel Attack
A general SCA attempts to obtain confidential data processed internally in a chip. The attacker analyzes the device's physical parameters, including supply current and physical emissions such as electromagnetic fields and execution time. This information is exploited to break cryptography to view the message before it is encrypted. These attacks pose a severe threat to modules that integrate cryptographic systems.(2)
Power Analysis SCA exploits the power consumed by the device to reveal the message sent by the device. A successful attack only requires a low-end oscilloscope, a connection to the device's power supply, and open-source software to attack the device.
In an Electromagnetic SCA, instead of power analysis, an attacker measures the electromagnetic emissions from the device and performs signal analysis on them.
Fault Injection Attack
A Fault Injection Attack (FIA) injects a fault into an embedded system to change its intended behavior. FIAs are used to bypass secure boot mechanisms, extract a secret key, leak confidential data, push malicious data upstream or downstream, or disable SCA countermeasures.
Glitching Attacks (GA) are common FIAs. In Voltage Glitch Attack, sudden changes in the supply voltage are created, which are usually negative and induce transient faults. These faults disrupt the internal logic causing computational faults. The equipment needed is a configurable pulse generator that can drive low voltages, often available as integrated FPGAs for less than $500.
Electromagnetic Fault Injection (EMFI) uses small coils to inject highly localized electromagnetic fields, generated in either transient or harmonic configurations and directed towards a specific component into a device. Such fields manipulate the system power device clock and introduce localized thermal variations.
Invasive Attacks
Invasive attacks such as delayering and modification of the circuit are tamper attacks that require direct access to the device's internal components. They usually demand a knowledgeable and well-equipped attacker to succeed. The attacker physically tampers with the metal wires using microprobes to alter the circuit behavior by overdriving the chip.(3)
Remote Physical Attacks
The two most well-known remote physical attacks are Rowhammer and Plundervolt.
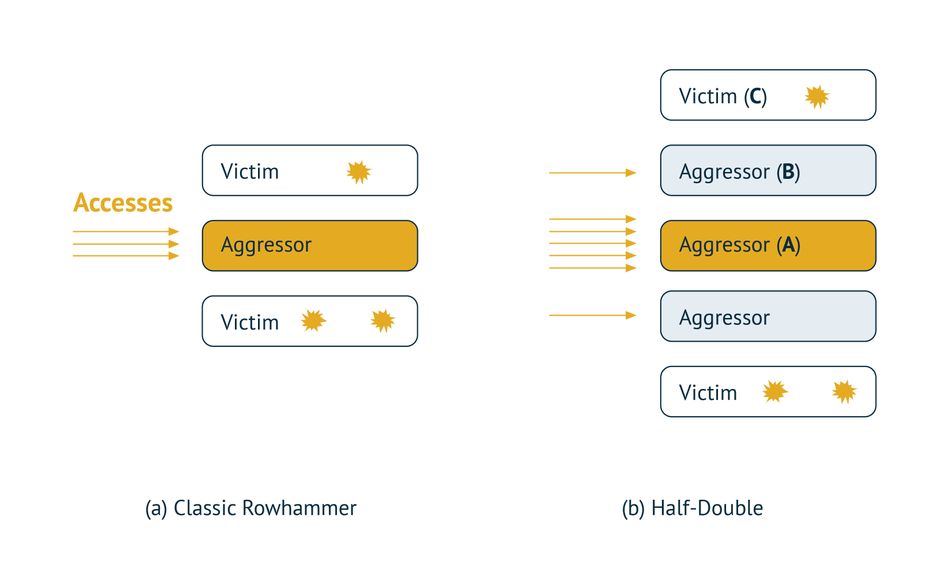
Rowhammer Attack
The Rowhammer bug is a hardware reliability issue with new generation DRAM chips in which repeatedly and rapidly accessing (hammering) a row of memory can cause bit flips in adjacent rows, i.e., changing their bit values from 0 to 1 or 1 to 0.(5)
By utilizing the Rowhammer bug, the attackers corrupt the chosen data. Researchers from Google accessed the kernel memory by using a memory massaging technique to trigger the Rowhammer bug and force the kernel out of memory error. In this instance, the attackers can scan the memory for specific data, bypass established security mechanisms, and execute the attack primitives in security-critical areas.
Plundervolt Attack
Plundervolt attack exploits the "voltage regulator" feature of new Intel chips, intended to improve their efficiency and performance. The attacker uses this mechanism to reduce the core chip voltage methodically until a fault occurs.
Using these induced faults, the attacker can breach the chip's built-in set of security-based instruction codes, known as Software Guard Extensions (SGX). SGX protects sensitive data housed on Intel CPUs by storing it in secure areas separate from other memory.
Local Logical Attacks
The logical attacks aim to disrupt the logical flow of the device’s operations either by physically accessing the device and then launching an attack or using the services and trafficking hacks.
Local logical attacks are typically launched by exploiting JTAG, serial, and USB interfaces. Accessing these interfaces creates many possibilities, such as a reach to the controller's internal memory, which can lead to:
Manipulation of the register values,
Insertion of malicious data and code, and
Extracting, patching, and re-flashing the modified vulnerable/malicious firmware back into the device.
Remote Logical Attacks
Attackers usually launch remote logical attacks by exploiting the device’s operations via abundant requests or buffer overflows.
Buffer Overflow Attack
Buffers are memory storage regions that temporarily hold data while transferred from one location to another. If the size of data exceeds the capacity of the memory buffer, it overflows, and the program overwrites adjacent memory locations.
Attackers exploit buffer overflow issues by overwriting the memory of an application. This changes the program's execution path, triggering a response that damages files or exposes private information.(6) The attacker may load the erroneous data or malicious code and malfunction or destroy the SoC.
Flooding/Denial of Service (DoS) Attack
In these attacks, the targeted device is continuously bombarded with massive requests until it is overwhelmed and unable to respond to regular users. It eventually crashes, denying its services.
Conclusion
The massive rise in IoT devices has revealed their insecurities to expert security researchers, script gurus, and cybercriminals. They have found such weaknesses in IoT infrastructure that are exploited to launch inexpensive IoT attacks. These low-cost attacks threaten the security, confidentiality, and authenticity of their owner's systems and processes. The considerable variation in such attacks requires a comprehensive and innovative security approach which will be addressed in future articles in this series.
If you don’t want to wait for the next articles in this series to be published to learn more about these attacks and how to prevent them, you can download the full whitepaper Preventing A $500 Attack Destroying Your IoT Devices now. Download the full paper here.
References
- Hiter S. datamation.com. [Online].; 2021. Available from: https://www.datamation.com/trends/internet-of-things-iot-market/#:~:text=The%20IoT%20market%20reached%20%24761.4,2026%2C%20according%20to%20Mordor%20Intelligence.
- Seals T. threatpost.com. [Online].; 2021. Available from: https://threatpost.com/iot-attacks-doubling/169224/#:~:text=According%20to%20a%20Kaspersky%20analysis,more%20than%20twice%20the%20volume.
- Press R. rambus.com. [Online].; 2021. Available from: https://www.rambus.com/blogs/side-channel-attacks/.
- iotsecuritynews. iotsecuritynews.com. [Online].; 2018. Available from: https://iotsecuritynews.com/rampage-attack-explained-exploiting-rowhammer-on-android-again/.
- Imperva. imperva.com. [Online]. Available from: https://www.imperva.com/learn/application-security/buffer-overflow/.
About the sponsor: Intrinsic ID
Intrinsic ID is among the world’s leading providers of security IP for embedded systems based on physical unclonable function or PUF technology. The technology provides an additional level of hardware security utilizing the inherent uniqueness in each and every silicon chip. The IP can be delivered in hardware or software and can be applied easily to almost any chip – from tiny microcontrollers to high-performance FPGAs – and at any stage of a product’s lifecycle. It is used as a hardware root of trust to validate payment systems, secure connectivity, authenticate sensors, and protect sensitive government and military data and systems. Intrinsic ID security has been deployed and proven in millions of devices certified by EMVCo, Visa, CC EAL6+, PSA, ioXt, and governments across the globe.