CyberSpec turns machine learning onto the problem of spectrum sensor attacks, without overloading the host
The CyberSpec framework is designed to detect anomalous behavior linked to cyber-attacks against crowd-sensing spectrum sensors, even when said sensors are running on lightweight resource-constrained hardware like a Raspberry Pi.
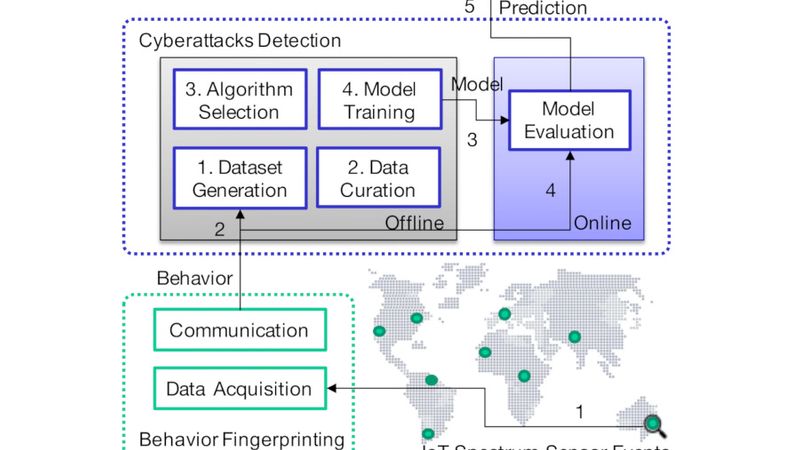
Designed to run on a Raspberry Pi-based spectrum sensor platform, CyberSpec can find an attack in 60 seconds.
The modern airwaves are thicker than ever: From smartphones and smartwatches to smart meters, smart homes, smart cars, and smart cities, there are more devices trying to communicate than ever before — and all trying to share an ever-crowded spectrum.
One possible solution is to make the communications systems smarter, monitoring the airwaves and allowing better management of scarce spectrum and improving how devices can coexist on a growing radio access network — but these integrated sensing and communication (ISAC) systems can be vulnerable to attack.
It’s this problem that a team from the Universities of Zurich and Murcia and the Swiss Department of Defense, Civil Protection, and Sports (DDPS) is aiming to solve with a machine-learning framework dubbed CyberSpec, designed to allow resource-constrained crowd-sensing spectrum sensors to detect — and hopefully thwart — a range of attacks.
Real-world validation
Where a number of academic projects are born in the lab, CyberSpec stands out: The team developed and deployed the system to a commercial crowd-sensing radio-frequency monitoring platform, ElectroSense. Designed specifically to address the growing burden placed on wireless communication networks, ElectroSense monitors the current occupancy of a given portion of spectrum and uses cognitive radio network (CRN) technology to shuffle devices off to currently under-utilized bands.
In the wild, rather than in the lab, ElectroSense and similar devices need to be robustly protected against attack — which is where CyberSpec comes in.
“CyberSpec [is] an ML/DL [Machine Learning/Deep Learning]-oriented framework using device behavioral fingerprinting to detect anomalies produced by SSDF [Spectrum Sensing Data Falsification] attacks affecting resource-constrained spectrum sensors,” the team writes of the concept.
The key: “Resource-constrained.” The ElectroSense platform is designed to run on commercial off-the-shelf Raspberry Pi single-board computers, which lack the heavy computational power often associated with deep learning approaches to behavioral fingerprinting. CyberSpec, the team claims, can work within these constraints — using machine learning techniques without harming the performance of the ElectroSense system itself, despite the relatively modest specifications of the hardware they share.
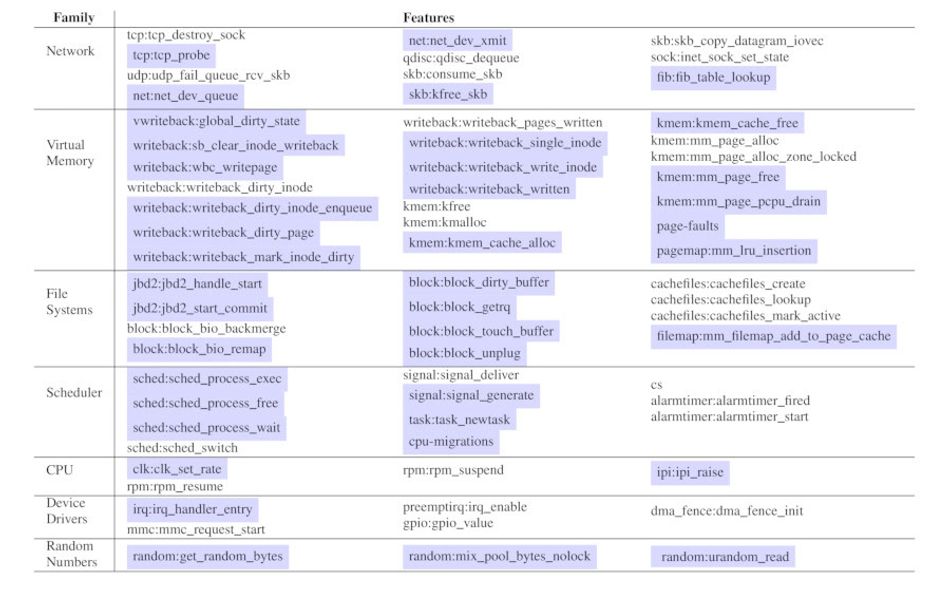
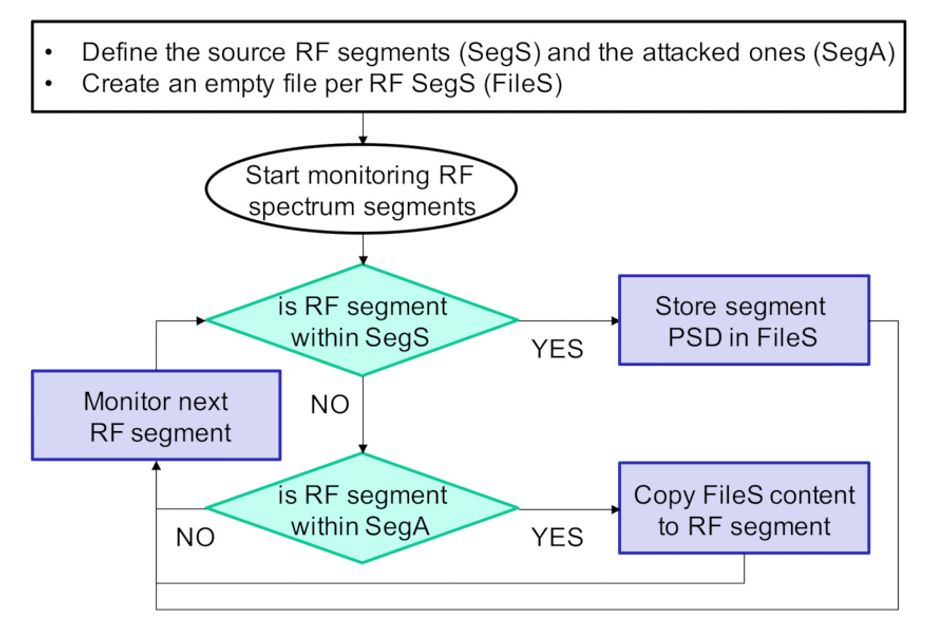
The CyberSpec framework, as tested, has two aspects. The first is its behavioral fingerprint capabilities, wherein it monitors the internal behavior of the sensor on which it is deployed and creates fingerprints to which future behavior can be compared.
The fingerprints are generated based on monitoring of a range of internal metrics: Network traffic, virtual memory allocations, file system operations, the system scheduler, system calls, CPU utilization, device driver loading and unloading, and random number generation systems — all things which can be monitored in real-time without straining the host system.
The second aspect is the detection of cyber-attacks, in which the fingerprints are used as training data for machine and deep learning algorithms in order to produce a system capable of detecting anomalies.
Defining and detecting the problem
First, though, there was the problem of definition. As the researchers point out in their paper, there is currently no universally-accepted formal definition of the behavior and impact of SSDF attacks — a problem when it comes to detecting the fingerprints of said behavior.
To overcome this, the team defined seven novel SSDF attacks: Repeat, Mimic, Confusion, Noise, Spoof, Freeze, and Delay. The seven cover three main attack types: The simulation of non-existent communications; hiding illegal transmissions or otherwise unwanted data; and performing both actions simultaneously.
With the attacks defined and ready for deployment, the team was able to test out the CyberSpec system on its ElectroSense crowd-sensing spectrum sensor network — and the results it delivered impress.
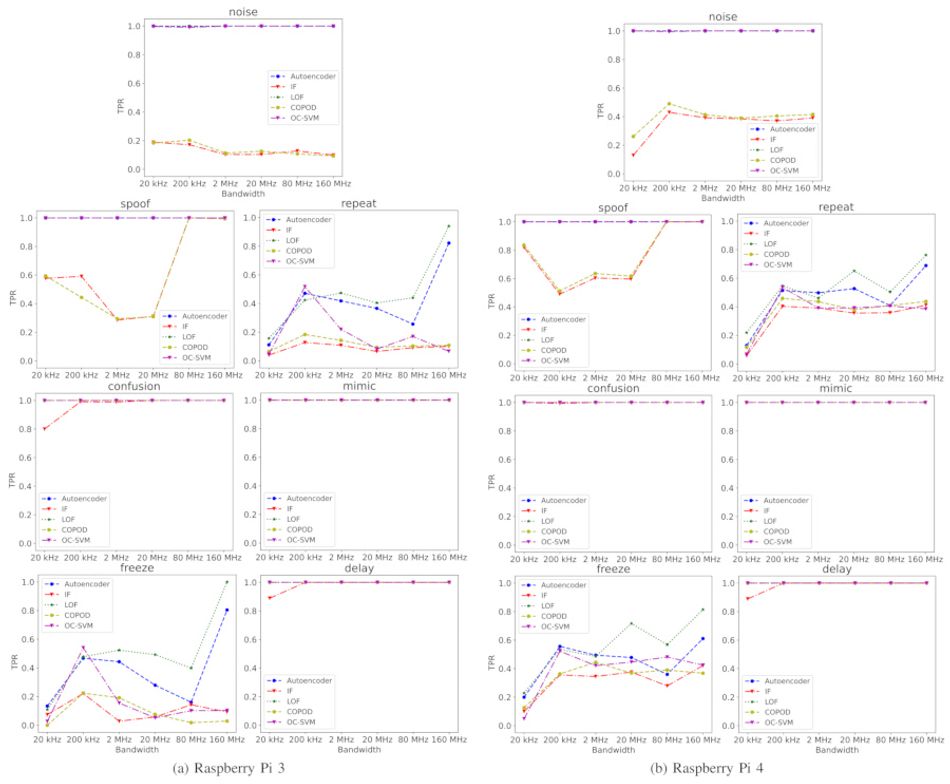
With the fingerprinting module running directly on each ElectroSense node, and the attack detection module running on a trusted central server, the CyberSpec framework was able to generate a baseline fingerprint of normal operations based on eight days’ operation then successfully and quickly detect the Noise, Spoof, Confusion, and Mimic attacks in all tested configurations.
Repeat and Delay, however, proved more challenging: “They are not adequately detected,” the researchers note, “until the affected bandwidth reaches 80 and 160MHz,” and even then only when using using one specific model — Autoencoder — of the five tested. Interestingly, the detection of these attacks is indirect: “When the affected bandwidth is sufficient,” the team writes, “the attack impacts the rest of the monitored events, and these variations are slightly detected.”
Freeze, in turn, was found to evade detection — but the researchers believe they know why, and how to resolve it: “CyberSpec does not monitor read file operations,” they write, “and the behavior of these attacks relies on that.”
For the attacks it can detect, though, CyberSpec proved impressively capable: The framework can, the researchers found, determine the difference between normal operations and an active attack in under 60 seconds, and with a very low computational cost to the host device.
The team has indicated its future work will focus on scalability to larger numbers of monitored devices, add privacy-preserving mechanisms like federated learning to prevent private data from being transmitted off-device, the use of supervised algorithms for attack classification, and adding new events to the monitoring system to resolve the issues in detecting Repeat and Freeze attacks.
The paper on CyberSpec is available under open-access terms on Cornell’s arXiv.org preprint server.
Reference
Alberto Huertas Celdrán, Pedro Miguel Sánchez Sánchez, Gérôme Bovet, Gregorio Martínez Pérez, Burkhard Stiller: CyberSpec: Intelligent Behavioral Fingerprinting to Detect Attacks on Crowdsensing Spectrum Sensors. DOI arXiv:2201.05410 [cs.CR]